All Categories
Network Security Fundamentals
Essential network security concepts including firewalls, VPNs, intrusion detection systems, and secure network architecture. Learn how to protect networks from unauthorized access, attacks, and vulnerabilities.

Data Encryption and Protection
Master encryption techniques for securing sensitive data at rest and in transit. Explore symmetric and asymmetric encryption, hashing algorithms, digital signatures, and key management strategies for comprehensive data protection.

Malware and Threat Prevention
Comprehensive malware defense strategies covering viruses, trojans, ransomware, spyware, and zero-day exploits. Learn threat detection, prevention techniques, antivirus solutions, and incident response procedures.

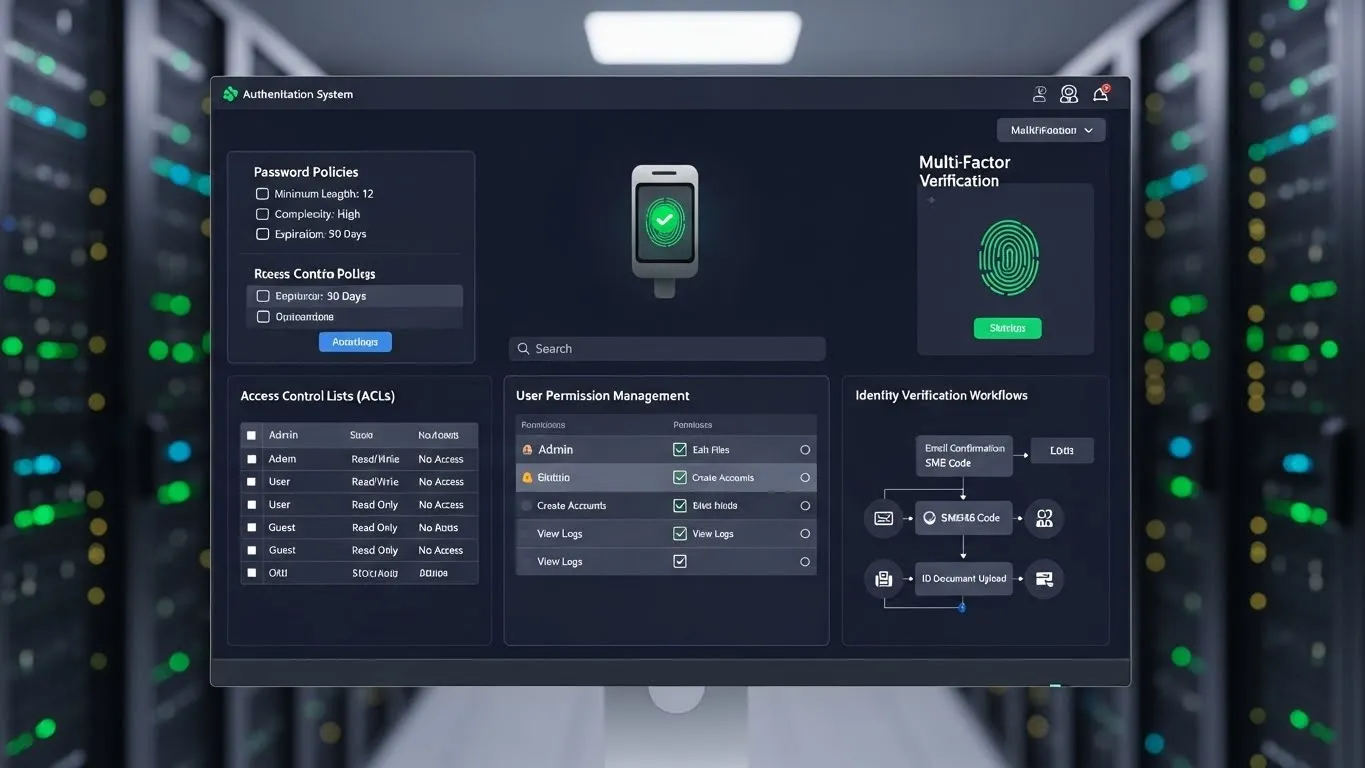
Authentication and Access Control
Implement robust authentication mechanisms including multi-factor authentication, biometrics, single sign-on, and role-based access control. Secure user identities and manage access privileges effectively.

Web Application Security
Protect web applications from common vulnerabilities including SQL injection, XSS, CSRF, and authentication flaws. Learn secure coding practices, OWASP Top 10 defenses, and penetration testing methodologies.

Cloud Security and Privacy
Secure cloud environments with best practices for AWS, Azure, and Google Cloud. Cover identity management, data encryption, compliance, container security, and cloud-specific threat protection strategies.

Incident Response and Recovery
Develop effective incident response plans for security breaches, data leaks, and cyberattacks. Learn forensic analysis, containment strategies, recovery procedures, and post-incident reviews for business continuity.

Security Awareness and Best Practices
Build security-conscious culture through employee training on phishing, social engineering, password hygiene, and safe browsing. Implement security policies, compliance programs, and continuous education initiatives.